Everything you need to know about the Bash Bug vulnerability in Ireland
The Bash Bug vulnerability (CVE-2014-6271)
A new critical vulnerability, remotely exploitable, dubbed “Bash Bug”, is threatening billions of machines all over the world.
The vulnerability was discovered by the security researcher Stephane Chazelas at Akamai firm.
It affects Linux and Unix command-line shell, aka the GNU Bourne Again Shell, and for this reason it is potentially exposing websites, servers, PCs, OS X Macs, various home routers, and many other devices to risk of cyber attacks.
The team Bash stands for the GNU Bourne Again Shell and refers to a Unix shell, which is an interpreter that allows users to send commands on Unix and Linux systems, typically by connecting over SSH or Telnet.
The Bash can also operate as a parser for CGI scripts on a Web server. Stephane explained that the vulnerability has existed for several decades and it is related to the way Bash handles specially-formatted environment variables, namely exported shell functions.
A shell gives both administrators and attackers high privileged access to operating system features, allowing them to run almost any command.
“The potential is enormous – ‘getting shell’ on a box has always been a major win for an attacker because of the control it offers them over the target environment,” said software architect and Microsoft MVP Troy Hunt.
An attacker could dump all data stored on a server, change its settings, or serve malicious code to infect the machine.
“There are many, many examples of exploits out there already that could easily be fired off against a large volume of machines.”
The National Institute of Standards and Technology has assigned the vulnerability the designation CVE-2014-6271, rating the severity of the remotely exploitable vulnerability as a “10″ on its 10-point scale.
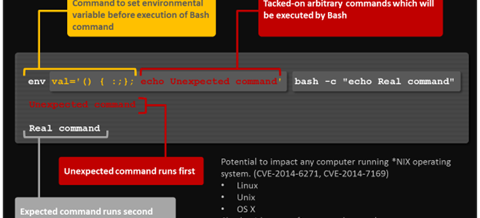
The critical Bash Bug vulnerability, also dubbed Shellshock, affects versions GNU Bash versions ranging from 1.14 through 4.3. A threat actor could exploit it to execute shell commands remotely on a targeted machine using specifically crafted variables.
To run an arbitrary code on a system running software which embeds a Bash, it is necessary to assign a function to a variable. Trailing code in the function definition will be executed.

Figure 1 – Shellshock command diagram (Symantec)
“GNU Bash through 4.3 processes trailing strings after function definitions in the values of environment variables, which allows remote attackers to execute arbitrary code via a crafted environment, as demonstrated by vectors involving the ForceCommand feature in OpenSSH sshd, the mod_cgi and mod_cgid modules in the Apache HTTP Server, scripts executed by unspecified DHCP clients, and other situations in which setting the environment occurs across a privilege boundary from Bash execution,” states the description for the Bush Bug flaw on the NIST National Vulnerability Database, which rated its severity as 10 out of 10.
Every machine having Bash configured as the default system shell could be easily hacked every time an application invokes the Bash shell command (e.g. Mail server) via HTTP or a Common-Gateway Interface (CGI).
The attacker could run arbitrary code on the server just by sending a specially crafted malicious web request by setting headers in a web request, or by setting weird mime types. Searching on the Internet, it is possible to find the source code for cgi-bin reverse shell reported below:
Similar attacks are possible via OpenSSH. “We have also verified that this vulnerability is exposed in ssh—but only to authenticated sessions. Web applications like cgi-scripts may be vulnerable based on a number of factors; including calling other applications through a shell, or evaluating sections of code through a shell,” Stephane warned. But if an attacker does not have an SSH account, this exploit would not work.
As reported in the advisory published by the NIST, the critical instances where the Bash Bug may be exposed include:
Apache HTTP Server using mod_cgi or mod_cgid scripts either written in bash, or spawn subshells.
Override or Bypass ForceCommand feature in OpenSSH sshd and limited protection for some Git and Subversion deployments used to restrict shells and allow arbitrary command execution capabilities.
Allow arbitrary commands to run on a DHCP client machine, various Daemons and SUID/privileged programs.
Exploit servers and other Unix and Linux devices via Web requests, secure shell, Telnet sessions, or other programs that use Bash to execute scripts.
Billions of servers affected by the Bash Bug flaw
The impact of the Bash Bug vulnerability is widely extended. Bash is commonly used to execute commands on a server, especially those sent by other programs and applications. Security experts are considering the severity of this vulnerability higher than the one assigned to the Heartbleed bug, and the most concerning issue is the low level of complexity needed to run an attack which exploits it.
“The first reason is that the bug interacts with other software in unexpected ways. We know that interacting with the shell is dangerous, but we write code that does it anyway. An enormous percentage of software interacts with the shell in some fashion. Thus, we’ll never be able to catalogue all the software out there that is vulnerable to the bash bug,” states Robert Graham on his Blog Errata Security.
“They go on to rate it a “10 out of 10″ for severity or in other words, as bad as it gets. This is compounded by the fact that it’s easy to execute the attack (access complexity is low) and perhaps most significantly, there is no authentication required when exploiting Bash via CGI scripts. The summary above is a little convoluted though so let’s boil it down to the mechanics of the bug,” added the security expert Troy Hunt.
The Bug Bash flaw is particularly dangerous for Internet-of-Things devices like smart meters, routers, web cameras and any other device that runs software, which allows bash scripts. Typically, such software is not easy to fix and are more likely to expose the critical flaw in the Internet.
As said by Graham, “Unlike Heartbleed, which only affected a specific version of OpenSSL, this bash bug has been around for a long, long time. That means there are lots of old devices on the network vulnerable to this bug. The number of systems needing to be patched, but which won’t be, is much larger than Heartbleed.”
According the results of a recent survey conducted by the Internet services company Netcraft, the number and types of Web servers being used worldwide is more than 1 billion servers, and that more than half of those are Apache servers which run Linux and thus contain Bash by default.
Threat actors are exploiting the Bash Bug vulnerability in the wild
According to security experts, the Bash Bug vulnerability may already have been exploited in the wild by threat actors to hit Web servers.
Attackers are already targeting the Bash vulnerability, less than 24 hours after the public disclosure of details about the flaw vulnerability. To date, an unknown number of devices may contain the flaw, including millions of stand-alone Web servers, Unix and Mac OS X systems, and numerous other Internet-connected devices.
Malware researchers speculated that the critical flaw may be exploited by attackers which manage botnets to exploit a large number of machines exposed on the Internet.
The list of potential targets is very long and includes home routers, medical equipment, SCADA/ICS devices and many other systems. For this reason, the Bash Bug is considered by security experts more dangerous than the Heartbleed flaw which affected only versions of OpenSSL released over a two-year period. According to the experts, the Bash bug has is a 25 five year old flaw, and also recent versions of Linux machines are potentially as exploitable as outdated servers.
The real problem resides in the low complexity of a Bash Bug based attack, for threat actors it is quite easy to run them against vulnerable servers
Pierluigi Paganini
ShareOCT
2014
